API Security Best Practices Checklist in 2024
 Marketing IBTI#Marketing IBTI
Marketing IBTI#Marketing IBTI
Are you losing sleep worrying about hackers breaking into your app and stealing important user information? Do you feel overwhelmed by the increasing threats of cyberattacks and unsure how to protect your applications? If you said yes to either of these questions, this topic is solely for you.
Today, APIs (Application Programming Interfaces) are the building blocks of many of the apps and services we use daily. They allow different pieces of software to connect and share information.
But just like any door to your house, APIs need to be secure to protect your valuable data. This is where our API Security Best Practices Checklist can help!
Why API Security Matters?
API security is all about making sure that only the right people and programs can use your API. It protects the data shared between clients (like apps or websites) and servers (where data is stored) from being accessed by hackers or unauthorized users.

According to a report by Traceable AI on API security in 2023:
- 60% of companies said they had a data breach in the last two years.
- Out of these, 74% experienced at least three data breaches related to APIs.
- Even more worrying, 40% had five or more API-related breaches.
- And 11% had over seven API-related breaches.
These numbers show how important it is to improve API security.
What is an API Security Best Practices Checklist and How to Use It?
An API security checklist is a list of important steps you need to take to keep your API safe from hackers and other cyber threats.
Each time you update or change your API, you should run through this checklist to make sure you haven't accidentally created any new security holes.
Here is the Rest (a software architecture style) API Security Best Practices Checklist to secure your API.
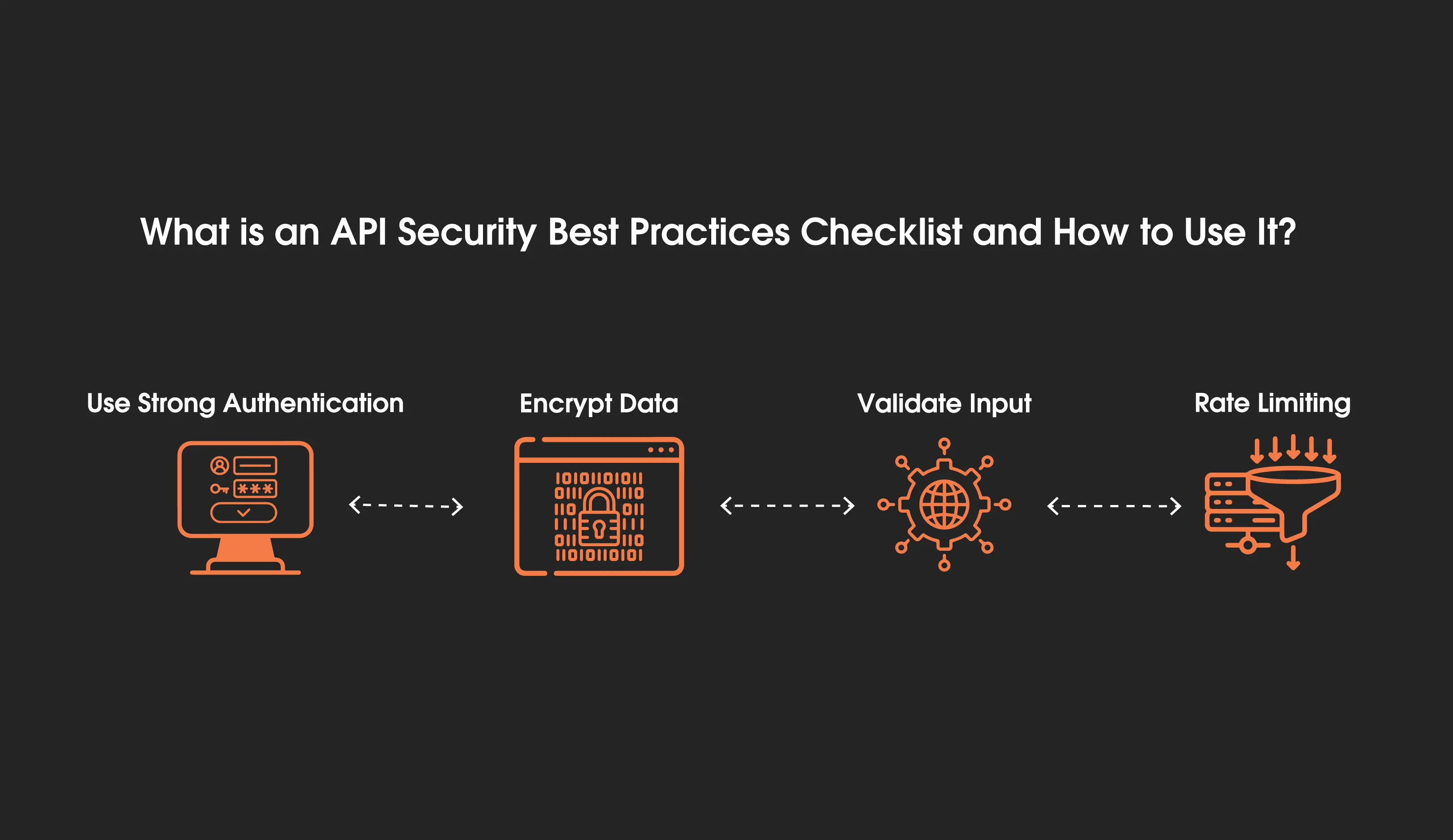
Use Strong Authentication
Ditch basic passwords! Use strong ways to check who is logging in, like:
- Multi-Factor Authentication (MFA): This needs a second step to log in, like a code sent to your phone.
- API Keys: Here, special codes are given to users who are allowed to use your API.
- OAuth: A secure way for users to log in with a trusted service (like Google) and then use your API.
What not to do:
- Don't rely on basic username/password combinations. They are easy for hackers to guess or steal.
Encrypt Data
Protect data when it's moving and stored using encryption protocols like:
- Transport Layer Security (TLS): Encrypts data sent between your API and users, stopping hackers from spying or changing the data.
- Data Encryption at Rest: Encrypts important information stored in databases, which adds extra security.
What not to do:
- Don't send sensitive data (like passwords or credit card details) without encryption. Hackers can easily steal this information.
Validate Input
Treat all user input with suspicion. Validate it to prevent malicious attacks:
- Sanitize user input: Remove harmful characters or code, like special characters, script code, or SQL code from user-provided data.
- Input validation checks: Make sure data matches expected formats (like email addresses or phone numbers).
- Input length restrictions: Limit how much data a user can submit to prevent attacks that overload the system.
What not to do:
- Don't blindly trust user input. Hackers can insert harmful code or change data to break into your API.
Rate Limiting
Set limits on API requests to prevent abuse:
- Limit by user/IP address: Restrict how many requests a user or IP address can make in a certain time.
- Limit by API endpoint: Set different limits for different parts of the API based on their importance.
- Implement throttling: Slow down requests that exceed the limit to avoid overload.
What not to do:
- Don't leave your API open to unlimited requests. This can cause Denial-of-Service (DoS) attacks that can crash your API.
Example: A ticketing API limits the number of purchase requests a user can make and slows down extra requests to prevent bots from buying all the tickets.
Use HTTPS
Enforce HTTPS for all API communication:
- HTTPS: A secure communication method that encrypts data using TLS.
- Enable HTTPS by default: Set up your API to accept HTTPS connections only.
What not to do:
- Don't rely on HTTP for API communication. It doesn't encrypt data, which makes it easy for hackers to intercept.
Example: A banking API uses HTTPS only, which ensures that user account information and fund transfers are secure.
Regular Security Testing
Find and fix security issues early:
- Vulnerability Scans: Automated tools that check your API code for weak spots. These tools crawl your API like a user would, testing for vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication methods.
- Penetration Testing: Ethical hackers try different attacks on the API, like guessing passwords, finding missing security checks, or changing data to access customer info without permission. Penetration testing shares what it finds so the company can fix the problems before real hackers can use them.
- Regular Security Audits: Regular checks to find and fix security gaps.
What not to do:
- Don't wait for a security breach before testing your API. Regular testing helps catch issues before hackers do.
Example: A financial services company regularly hires ethical hackers to test their API and find security flaws, fixing them before cybercriminals can exploit them.
Monitor and Log Activity
Keep a watchful eye on your API's activity to detect suspicious behavior:
- Log all API requests and responses: Track who is accessing your API (user/IP), what data they are requesting (endpoints, parameters), and the responses they receive (data, error codes).
- Set up alerts for unusual activity: Define triggers for suspicious patterns, like a sudden surge in requests from a particular IP or attempts to access unauthorized resources.
- Analyze log data regularly: Review logs to identify potential threats and investigate any suspicious activity.
What not to do:
- Don't operate your API in a black box. Monitor activity to understand how it's being used and detect potential abuse.
Update and Patch Regularly
Maintain a secure environment by keeping your API software and dependencies up-to-date:
- Apply security patches promptly: Software vendors regularly release security patches to address vulnerabilities. Install them as soon as possible to prevent attackers from exploiting known weaknesses.
- Update API libraries and frameworks: Use the latest versions of libraries and frameworks your API relies on. These updates often include security fixes and improvements.
What not to do:
- Don't neglect software updates. Outdated software with known vulnerabilities is a prime target for hackers.
Implement Access Controls
Limit who can use your API based on their role and permissions:
- Role-Based Access Control (RBAC): Create user roles like admin, editor, and user, and give each role specific permissions to access certain parts of the API.
- Attribute-Based Access Control (ABAC): Grant access based on user details like location or department, in addition to their roles.
- Least Privilege Principle: Only give users the minimum access they need to do their jobs.
What not to do:
- Don't let anyone access everything in your API. Use access controls to stop unauthorized use.
Example: A project management API uses RBAC. Developers can create and edit projects, while clients can only view their assigned projects. This way, users can only access the data they need for their roles.
Use API Gateways
Use an API gateway to manage and secure your API:
- API Gateway as a Single Entry Point: Route all API traffic through the gateway for centralized security checks like authentication, authorization, and rate limiting.
- Offload Security Tasks: The API gateway handles security functions, which reduces the load on your backend servers.
- Extra Features: Many API gateways offer features like traffic management, analytics, and monetization options.
What not to do:
- Don't create your solution from scratch. Use API gateways to simplify security and improve efficiency.
Example: A travel booking API uses an API gateway. The gateway checks that all requests are authenticated, validates user tokens and limits the number of requests to prevent abuse. It also provides insights on how the API is used through built-in analytics.
In addition, you can visit our blog to get a thorough idea of the API development process.
Why Choose IBTI for the Best API Development
You can choose IBTI for the best API development because we create APIs that automate your tasks and connect your apps smoothly.
We'll create custom, secure APIs that perfectly fit your needs, so you can focus on running your business!
Let IBTI turn your ideas into success!
You can visit our informative blog to learn where to find the best custom API development company in the USA.
Wrapping Up
By following the above-mentioned API Security Best Practices Checklist, we hope that you can take a big leap toward securing your APIs. Remember, API security is an ongoing process. By staying vigilant and keeping your security measures up-to-date, you can help protect your data and keep your apps and services running smoothly.

Marketing IBTI
#Marketing IBTI🇧🇷 Português
A IBTI é uma empresa de tecnologia com mais de 12 anos de experiência em desenvolvimento de sistemas, apps e soluções sob demanda. Atuamos no Brasil e no exterior com foco em qualidade, inovação e eficiência.
🇺🇸 English
IBTI is a tech company with over 12 years of experience developing custom software, apps, and IT-as-a-service solutions. We serve clients in Brazil and abroad, with a strong focus on quality, innovation, and efficiency.